What do the following websites all have in common?
- www.bcpcouncil.gov.uk
- www.cardiff.gov.uk
- www.middlesbrough.gov.uk
- www.hastings.gov.uk
- www.arun.gov.uk
- www.bristol.gov.uk
- www.medway.gov.uk
- www.plymouth.gov.uk
The obvious (and correct) answer is they're all UK Council websites. But the more nuanced answer is that they have all been victims of Distributed Denial of Service (DDoS) cyber attacks today.
As a quick explainer, a DDoS attack is where a bad actor engineers multiple simultaneous requests to a website from a network of computers they control. Once scaled up, the number of incoming requests overwhelm the resources of the server hosting a website, and it can no longer respond to any requests, including those of legitimate users.
How do we know this? Because the perpetrators claim responsibility for the attacks on X!
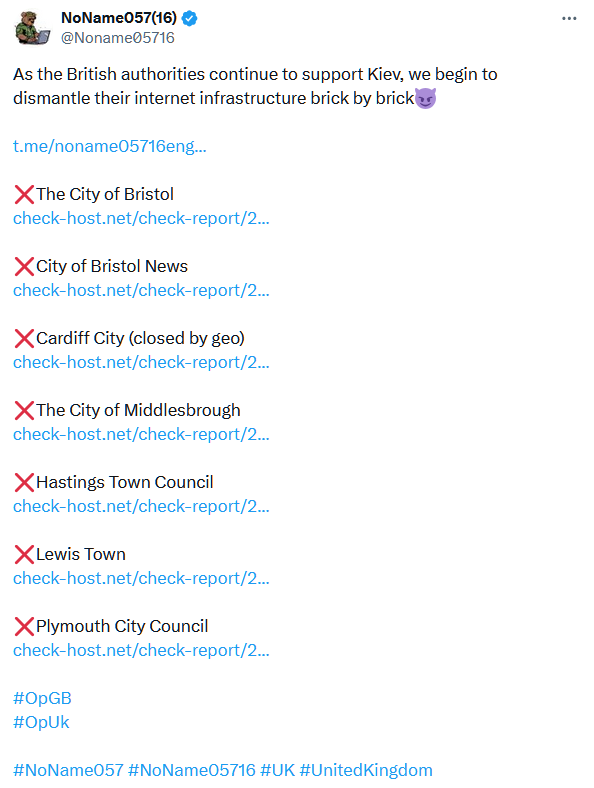
Today's DDoS attack originated from a Russian group called NoName057 - https://en.wikipedia.org/wiki/Noname057(16). They have a unique setup in that NoName057 run the system for organising DDoS attacks through a Telegram channel, and the actual DDoS attacks are from third parties who use NoName057’s custom software, and these third parties earn a cryptocurrency called TON which is also managed by NoName057. From what we’ve seen, NoName057 publish a list of target sites and exploit patterns on a daily basis for their network to attack. They mainly target Ukrainian sites, but add in a specific country to attack each day.
A few weeks ago, one of our clients was the victim of such an attack, along with about a dozen or so UK local authorities. What we saw there was a DDoS attack consisting of about 3000 IPs making requests at the rate of 1 request every 3 seconds or so. The requests followed a small number of URL patterns and request types. The sheer volume of requests, at around 1000 page requests per second, immediately overwhelmed the server.
The steps to getting the server back on its feet were as follows:
- We needed to adjust the web server config to return "service unavailable" responses for the DDoS requests, before the website CMS application received them.
- We needed to increase the maximum number of files that could be open on disk, as the server had hit its limits from the number of sockets that were open returning responses to the DDoS requests.
- Longer term, we placed Cloudflare as a proxy to the server. Cloudflare offer specialist services to filter and absorb DDoS requests. Their infrastructure acts as a shield to your web server, stopping the DDoS requests from reaching it. Similar products are offered by other vendors e.g. Amazon Web Services (AWS Shield) or Imperva DDoS Protection, they're all aiming to do the same thing. Your DDoS protection proxy will need to be in place before a DDoS attack happens, you can add it in after an attack is underway, but it's a lot more complicated (and stressful!).
These DDoS attacks look here to stay, so if you work at a UK local authority or public sector organisation, it's best to make preparations now on the assumption that sooner or later your site will be targeted. As an illustration, just this week, around 30 UK local authority websites have been targeted, with many sites showing visible signs of disruption as a result.
The only saving grace of the recent DDoS attacks is that attacks only seem to last for a 24-hour period before the target list is updated.
It's worth noting that as far as we're aware, no local authorities are receiving any support from central government organisations on how to prepare for or deal with these DDoS attacks.
At the time of writing, the following sites are all still down:
And these sites remain down from yesterday's attacks:
- mod.police.uk (the Ministry of Defence Police)
- www.cityofelycouncil.org.uk
If you need assistance on how to restore your site or prepare for a DDoS attack, then please contact us.